CyberSecurity.PH #040
7,000 people rescued from scam-centres; AI-powered threat detection and continuous scanning; Ghidra, AWS-Key-Hunter, AI ASCII-Smuggling-Hidden-Prompt-Injection; China sponsored Salt Typhoon threat actors continue to breach organizations; Threat actors tricking users linking Signal
Welcome to CyberSecurity.PH issue #040,
Still working hard to improve cybersecurity outcomes in the Philippines!
Philippines and South East Asia
7,000 people rescued from Myanmar scam-centres
Thailand's Prime Minister, Paetongtarn Shinawatra has announced that 7,000 people rescued from illegal call centre operations in Myanmar are due to be transferred to Thailand amid a crackdown on cross-border scam operations.
The rescue operation has been running for more than a week and Philippines nationals are already reported to be among those rescued.
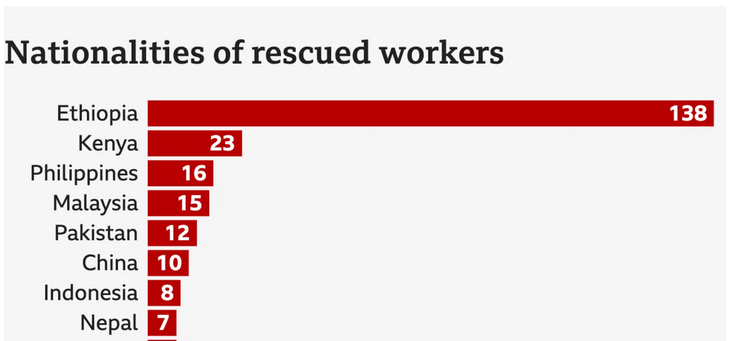
The crackdown is part of regional efforts to address scam-centers run by criminal syndicates in Myanmar, Cambodia and Laos that force victims into fraudulent online schemes where Thailand has been abused as a common transit point for victims trafficked away into these scam-centers.
Victims are often lured into these operations by social media job postings that promise well-paid technology roles that "require" relocation.
Victims trapped in these operations are forced to run online scams such as romance fraud, cryptocurrency scams and fake investment scams.
Further reading: Reuters, The Record, BBC
Google stops malicious apps with 'AI-Powered Threat Detection' and continuous scanning
Google has announced their progress in combating the enormous volumes of scam apps by leveraging artificial intelligence threat detection systems to handle the scale. Google Playstore applications for the Philippines are among the first regions to receive Google's new enhanced scam app detection and removal processing.
... investments included AI-powered threat detection, stronger privacy policies, supercharged developer tools, new industry-wide alliances, and more. As a result, we prevented 2.36 million policy-violating apps from being published on Google Play and banned more than 158,000 bad developer accounts that attempted to publish harmful apps.
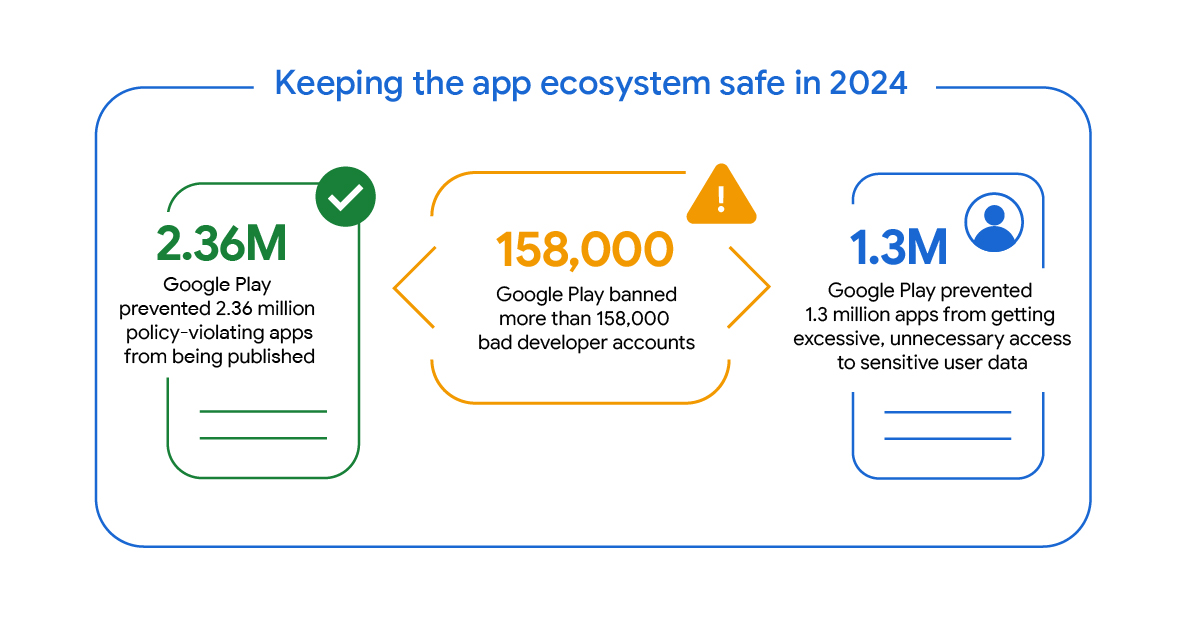
The Google Blog article states that nine regions, Brazil, Hong Kong, India, Kenya, Nigeria, Philippines, South Africa, Thailand, and Vietnam are now benefiting from AI enhanced and continuous threat detection.
Further reading: Google Blog (Feb 6th), Bleeping Computer, Google Blog (Jan 29th)
Cybersecurity Threat Landscape
Threat actors tricking users into linking devices to access Signal, WhatsApp and Telegram messages
Google Threat Intelligence Group (GTIG) has reported on their observations of Russian threat-actors targeting Signal, WhatsApp and Telegram messaging systems, particularly among those involved in the Ukrainian conflict.
The Signal app is highlighted as being the main target and this makes sense because Signal's security-by-design has made it popular among military personnel, politicians and journalists globally, not just in conflict zones.
The threats have been observed abusing the ability to "link" the messaging platforms with other devices, such as a web-browser that makes it possible to review all the messages of the victim and maintain persistence.
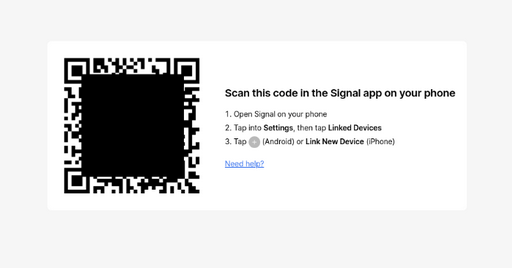
QR codes are commonly used in a way that the victim believes they are joining a group or chat, where-as they are in-fact phishing pages or other token stealing-proxies that end-up delivering the tokens and keys needed to link to the victims account.
Further reading: Google TIG, Hackread, The Record, Bleeping Computer, Dark Reading
China sponsored Salt Typhoon threat actors continue to breach telecom organizations
The Insikt Group, part of cybersecurity company Recorded Future, has delivered a new report that details the continued exploitation of international telecom companies between December 2024 and January 2025.
The report makes an important point on page one in the Executive Summary -
Unpatched public-facing appliances serve as direct entry points into an organizationʼs infrastructure.
It's really that simple.
Victim companies are not managing their external threat surface areas and are leaving vulnerable endpoints publicly accessible that makes it possible to create network pathways into inner networks.
The recent activity appears to be leveraging CVE-2023-20198 together with CVE-2023-20273 to gain root privileges on Cisco network devices - these vulnerabilities are at least 2 years old and are in active exploit.
Further reading: Recorded Future, Tech Crunch, The Register, Dark Reading
Russian threat-actors targeting MS365 accounts using device code authentication phishing
Cybersecurity company Volexity has released yet another deep-dive report into threat activity involving Russian threat actors.
From their report -
- Volexity has observed multiple Russian threat actors conducting social-engineering and spear-phishing campaigns targeting organizations with the ultimate goal of compromising Microsoft 365 accounts via Device Code Authentication phishing.
- Device Code Authentication phishing follows an atypical workflow to that expected by users, meaning users may not recognize it as phishing.
- Recent campaigns observed have been politically themed, particularly around the new administration in the United States and the changes this might mean for nations around the world.
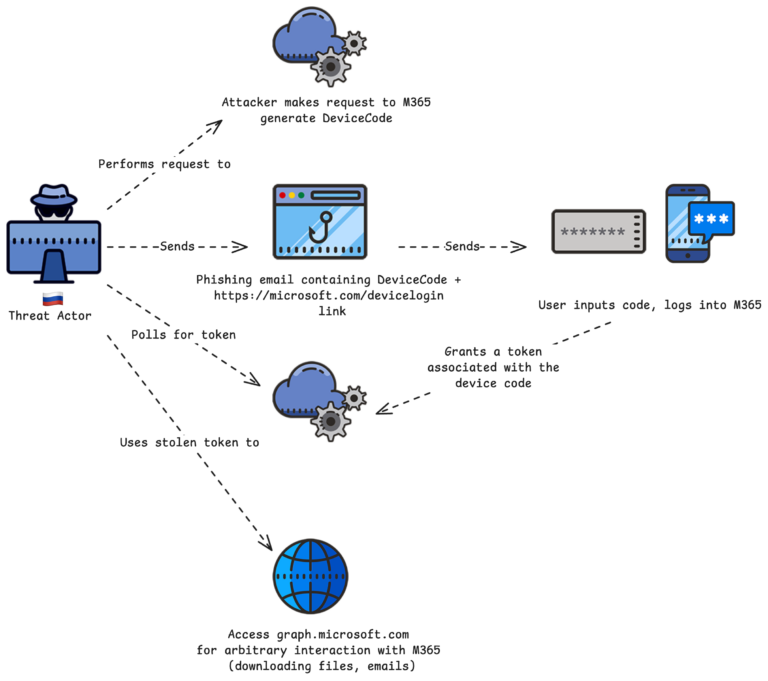
The Volexity report is detailed and provides excellent screenshots that cyber-defenders can use to teach their organizations about how these things look in the field, and indicators of compromise to help protect their organizations.
Cybersecurity Tools and Engineering
A weekly highlight on tools and other resources (often open-source) that we use, find useful or is just plain interesting; check out our engineering-section online at CyberSecurity.PH too!
- Ghidra - the NSA (US National Security Agency) software and reverse engineering framework (new 11.3 release) - github.com/NationalSecurityAgency/ghidra
- AWS-Key-Hunter - Find exposed AWS keys that your engineers have committed to Github and tried (but failed) to remove (hint, you cannot remove history from github even if you force a new main/master, credentials MUST be cycled if committed to git) - github.com/IamLucif3r/AWS-Key-Hunter
- ASCII-Smuggling-Hidden-Prompt-Injection - a novel approach to hacking AI assistants using Unicode Tags. This project demonstrates how to use Unicode Tags to hide prompt injection instruction to bypass security measures and inject prompts into large language models, such as GPT-4, leading them to provide unintended or harmful responses - github.com/TrustAI-laboratory/ASCII-Smuggling-Hidden-Prompt-Injection-Demo
Cybersecurity Vulnerabilities
Cisco ISE API allows authenticated remote code execution (CVSS 9.9)
A vulnerability in an API of Cisco ISE could allow an authenticated, remote attacker to execute arbitrary commands as the root user on an affected device. This vulnerability is due to insecure deserialization of user-supplied Java byte streams by the affected software. An attacker could exploit this vulnerability by sending a crafted serialized Java object to an affected API. A successful exploit could allow the attacker to execute arbitrary commands on the device and elevate privileges
Further reading: NIST.gov, The Hacker News
Palo Alto Networks vulnerability allows authentication bypass (CVSS 8.8)
An authentication bypass in the Palo Alto Networks PAN-OS software enables an unauthenticated attacker with network access to the management web interface to bypass the authentication otherwise required by the PAN-OS management web interface and invoke certain PHP scripts - CVE-2025-0108
This vulnerability is being chained with other known PAN-OS vulnerabilities in a way that has cause the vendor to issue statement with
"We are urging all customers with internet-facing PAN-OS management interfaces to immediately apply the security updates released on February 12, 2025,"
Further reading: NIST.gov, The Register, Dark Reading
FortiOS super-admin privilege escalation (CVSS 8.8)
An incorrect privilege assignment vulnerability [CWE-266] in Fortinet FortiOS version 7.6.0, 7.4.0 through 7.4.4, 7.2.0 through 7.2.9 and before 7.0.15 allows an authenticated admin whose access profile has the Security Fabric permission to escalate their privileges to super-admin by connecting the targeted FortiGate to a malicious upstream FortiGate they control.
Further reading: NIST.gov, Bleeping Computer, Hackread
Two OpenSSH vulnerabilities (CVSS 6.8)
- CVE-2025-26465 (CVSS score: 6.8) - The OpenSSH client contains a logic error between versions 6.8p1 to 9.9p1 (inclusive) that makes it vulnerable to an active MitM attack if the VerifyHostKeyDNS option is enabled, allowing a malicious interloper to impersonate a legitimate server when a client attempts to connect to it (Introduced in December 2014)
- CVE-2025-26465 (CVSS score: 5.9) - The OpenSSH client and server are vulnerable to a pre-authentication DoS attack between versions 9.5p1 to 9.9p1 (inclusive) that causes memory and CPU consumption (Introduced in August 2023)
Further reading: Qualys, The Hacker News, Bleeping Computer
Cybersecurity Engineering Overload
Exploiting "onerror" event in image tags to deploy payment skimmers
Cybersecurity company Sucuri has released an interesting article that reverse engineers a payment skimmer inserted into a victim webcart by using an "onerror" event that loads a skimmer hidden as an inline base64 encoded image data.
The article is a good read if you are into the deep technical end of exploits and code smuggling.
Further reading: Sucuri.net
