CyberSecurity.PH #041
Philippine Army confirms hack; Chinese Lotus Panda threat-group targeting APAC; FBI confirms Lazarus responsible for Bybit heist; Remote Code Execution in Microsoft Windows KDC; VMware actively exploited zero-day vulnerabilities; more cybersecurity tools and engineering
Welcome to CyberSecurity.PH issue #041,
Philippines and South East Asia
Philippine Army confirms hack by threat-actor Exodus Security
The Philippine Army has confirmed an attack on its systems according to footage posted by Radyo Pilipinas on Twitter (that X thing).
Just to give you the context dun nga sa indentification natin, but the specifics we cannot divulge because that’s part of the investigation. What we can say is we know the IP address na ginamit nila, we know where they are at kung sino-sino, and that’s all part of the investigation.” | via Col. Louie Dema-ala | Chief, Public Affairs Office Philippine Army
Unconventional cybersecurity news source Deep Web Konek made the hack well known on 22 Feb through a post on their (new) website. Following on from their initial report Deep Web Konek are now reporting that threat-actors are actively engaged in credential hunting (likely password stuffing) at various endpoints where exposed users are likely to have accounts, including universities and other government departments.
The Threat Actor going by the name "Exodus Security" has claimed responsibility for the hack and states they have acquired 10k personnel records belonging to active and former service members.
Further reading: Deep Web Konek, x.com/radyopilipinas1, The Record
Chinese Lotus Panda threat-group targeting APAC organizations with Sagerunex variants
Lotus Panda, a known Chinese threat group, has been observed targeting government, manufacturing, telecommunications, and media organizations sectors in the Philippines, Vietnam, Hong Kong, and Taiwan with malware known as Sagerunex.
Multiple sources are now reporting threat indicators via the Alien Vault OTX that defenders can use in their organizations.
Lotus Blossom has reportedly been using the Sagerunex backdoor since 2016 and uses long-term persistence shells to maintain a foothold inside organizations according to Cisco Talos researcher Joey Chen.
Further reading: Cisco Talos, The Hacker News
Threat actors impersonating Taiwan Taxation authority to deploy malware
Cybersecurity company Fortinet has released a post regarding their observations of specially crafted PDF files that give the receiver the impression they have a notice from the taxation authority in Taiwan.
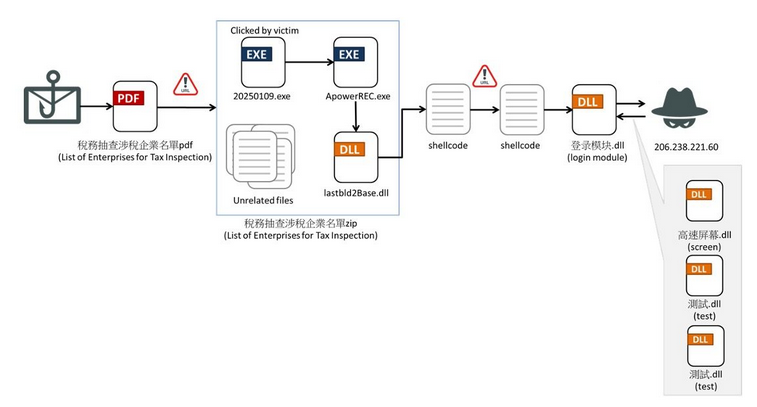
The assessment from the Fortinet Threat Research team is detailed and provides good indicators of threat that defenders can use to protect their organizations.
Further reading: Fortinet, HackRead
Solo hacker responsible for 90x high-profile data leaks arrested in Thailand
A 39-year-old Singaporean man linked to dozens of high-profile hacking cases in Thailand and other countries has been arrested in Bangkok. The arrest is the result of law-enforcement collaboration between Singapore and Thailand.
The solo hacker, who operated under the aliases ALTDOS, DESORDEN, GHOSTR and 0mid16B, has been among the most active cybercriminals in the Asia-Pacific region since 2021.
Further reading: Bangkok Post, The Record, Group IB
Cybersecurity Threat Landscape
FBI confirms Lazarus threat-group responsible for $1.5B Bybit crypto heist
The Bybit exchange theft has been big news in the past week considering threat-actors managed to take ~$1.46Bn in Ethereum (ETH) crypto currency.
The mechanism used by Lazarus threat-actors is fascinating, the understanding is that Lazarus exploited the fact that the tools used by Bybit exchange operators did not provide adequate observability on the ETH crypto-contract(s) involved and hence were not able to determine or understand they were in the middle of a heist until after the fact.
Plenty of excellent technical analysis to review, here are two to get started -
- https://www.certik.com/resources/blog/bybit-incident-technical-analysis
- https://hextrust.com/resources-collection/the-bybit-crypto-hack—an-analysis-by-hex-trust
The event is yet another sad reminder for crypto enthusiasts that unless there is enforcement capacity that is able and willing to defend a "currency" as an instrument of value store then that "currency" is a very risky instrument - while the Bybit CEO has bravely "declared war" to get monies back, his capacity to send real world warships and military assets is very limited - no warships, no army, no enforcement.
The US FBI has published a Public Service Announcement regarding that names North Korea as the threat origin and links a document that names the group as Lazarus; unfortunately, a mere FBI service announcement does not give effect to active enforcement action; Web3 is going just great.
Further reading: Bleeping Computer, The Register, The Record
Cybersecurity Tools and Engineering
- Redsheet - Red Teaming & Active Directory Cheat Sheet - github.com/expl0itabl3/Redsheet
- MSFTRecon - a reconnaissance tool for red teamers and security professionals to map Microsoft 365 and Azure tenant infrastructure - github.com/Arcanum-Sec/msftrecon
We really like the whole Arcanum-Sec repo. They've done a great job in collecting and maintaining red-team tools that represent well known techniques employed by threat-actors to compromise weak enterprises - defend your organization by understanding why they are effective and address those vulnerabilities.
Cybersecurity Vulnerabilities
Remote Code Execution in Microsoft Windows KDC Proxy (CVSS 9.8)
- CVE-2024-43639: A remote, unauthenticated attacker could direct KDC proxy to forward a Kerberos request to a server under their control, which would then send back a crafted Kerberos response. Successful exploitation could result in arbitrary code execution in the security context of the target service.
Further reading: Microsoft, Zero Day Initiative
WordPress Plugin code execution vulnerability with 10k installs (CVSS 9.8)
- CVE-2025-0912: The Donations Widget plugin for WordPress is vulnerable to PHP Object Injection in all versions up to, and including, 3.19.4 via deserialization of untrusted input from the Donation Form through the 'card_address' parameter. This makes it possible for unauthenticated attackers to inject a PHP Object. The additional presence of a POP chain allows attackers to achieve remote code execution.
Further reading: Wordfence, Cybersecurity News
VMware actively exploited zero-day vulnerabilities (CVSS 9.3)
- CVE-2025-22224: VMware ESXi, and Workstation contain a TOCTOU (Time-of-Check Time-of-Use) vulnerability that leads to an out-of-bounds write. A malicious actor with local administrative privileges on a virtual machine may exploit this issue to execute code as the virtual machine's VMX process running on the host.
- CVE-2025-22225: VMware ESXi contains an arbitrary write vulnerability. A malicious actor with privileges within the VMX process may trigger an arbitrary kernel write leading to an escape of the sandbox.
- CVE-2025-22226: VMware ESXi, Workstation, and Fusion contain an information disclosure vulnerability due to an out-of-bounds read in HGFS. A malicious actor with administrative privileges to a virtual machine may be able to exploit this issue to leak memory from the VMX process.
Further reading: Infosecurity Magazine, The Record, The Register
