CyberSecurity.PH #039
AI technologies; Malicious VPN installers; Fake wedding invites and Android malware; Thai arrest in $182m romance scam; Cracked and Nulled forums seized; Juniper backdoors in the wild; SonicWall critical vulnerability
Welcome to CyberSecurity.PH issue #039,
Working hard to improve cybersecurity outcomes in the Philippines over here!
Artificial Intelligence
An off topic start this week but very relevant to all knowledge-work disciplines (cybersecurity included).
Two weeks ago an AI reasoning model was made public (the DeepSeek R1 thing) and besides the very real cybersecurity concerns there is something quite special they have discovered and published regarding the model-development-techniques that is easy to miss given all the attention and concern on the product release.
Their model-building-techniques have made it clear that something called self-reinforcement learning is possible. Now that their technique is public-knowledge it means many AI developers are going to jump in to improve and expand on that technique. This little detail is likely to change the way most knowledge based tasks are performed, the extent of which is difficult to grasp in human terms.
This sounds like hyperbole and gross exaggeration, here’s why it matters.
Unless your cool AI/LLM tool can produce genuinely new-knowledge that humans have not discovered then the tool is not much more than a very-useful but elaborate auto-compete tool - this is the detail that has changed with these reasoning model techniques and it means machines (ie AI/LLM models) are able to self-discover new knowledge that in-turn makes it possible for the model to learn from that new knowledge in a constant feedback loop, thus making new discoveries that humans will not have time to achieve.
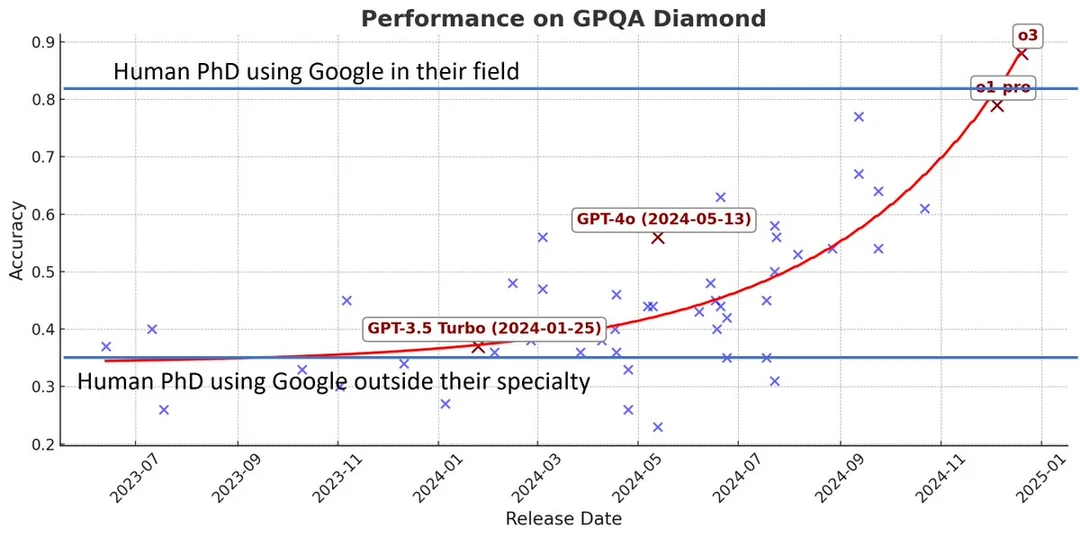
The DeepSeek R1 model is not the only reasoning model out there, and it is likely to be surpassed by another [see: OpenAI O3], however the public, free and open release of these model building techniques has changed the knowledge discovery landscape that will have an impact on workers that use a keyboard - particularly cybersecurity.
Finally, the DeepSeek R1 reasoning model is lovely, please understand the modes-of-threat that come with it. Have a read of our Understanding modes-of-threat in DeepSeek and other AI technologies article that we've made as easy to read and understand as possible.
Further reading: Prof. Ethan Mollick, Situational Awareness
Philippines and South East Asia
China-linked threat actor "PlushDaemon" targets victims in South East Asia with malicious VPN installers
Cybersecurity company ESET have issued a report that details how the software installer of a VPN provider in South Korea (IPany) was compromised back in 2023 by replacing their installer with one that also delivers malware attributed to "PlushDaemon" throughout that time.
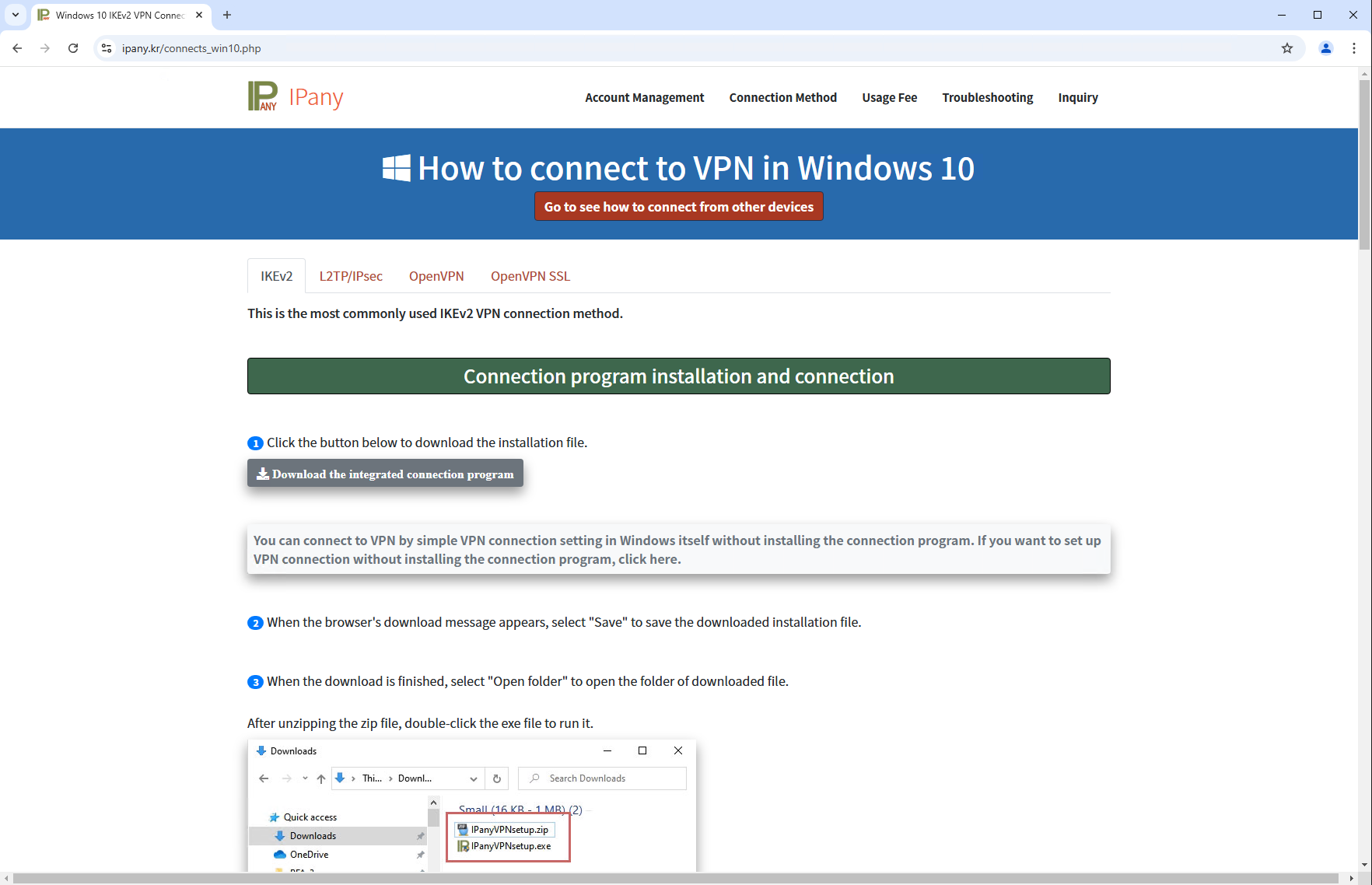
ESET states that the PlushDaemon threat-group has not previously been identified, however their threat tool-chains are well developed with ~30 backdoor components for cyber threat activities.
The ESET report states -
- PlushDaemon is a China-aligned threat group, engaged in cyberespionage operations.
- PlushDaemon’s usual initial access vector is by hijacking legitimate updates of Chinese applications, the supply-chain attack against IPany is not their usual mode of operation.
- PlushDaemon is the only threat-group that have some of the component implants suggesting they are a capable threat actor.
- The so-called "SlowStepper" malware discovered via the IPany VPN installer has a large toolkit composed of ~30 components.
- The PlushDaemon threat group has likely been active since 2019, against entities in China, Taiwan, Hong Kong, South Korea, the United States, and New Zealand.
Further reading: We Live Security (ESET), The Record, The Hacker News, Cyber Security News
Fake wedding invites, parcel delivery notifications, and government job offers used to spread Android malware
Cybersecurity company Kaspersky (yes, a Russian company) has issued a report that details a malicious campaign targeting victims in Malaysia and Brunei with malware that has tell-tale signs of being written by an Indonesian-speaking threat actor.
Kaspersky have named this campaign "Tria Stealer" and the report details how it operates -
- Collecting victims’ SMS data, tracks call logs, messages from WhatsApp and email data from Gmail and Outlook.
- Exfiltrates data by sending it to various Telegram bots using the Telegram API for communication.
- The threat actor(s) then exploit the stolen data to hijack personal messaging accounts, impersonate account owners to request money transfers, and compromise accounts with other services.
The report is long and detailed with an excellent collection of indicators-of-compromise and attributes that cyber-defenders can use.
Further reading: Securelist (Kaspersky), The Record
Thai police arrest woman linked to $182m romance scam
The story on the 2019 romance scam involving the CFO of EssilorLuxottica (think RayBan sunglasses) is eye opening particularly in terms of how the victim was groomed and manipulated over an extended period.
According to Thailand’s Central Investigation Bureau (CIB), law enforcement have now arrested a 52-year-old woman Hat Yai International Airport in the country’s south. The woman is accused of opening bank accounts at the behest of her Nigerian boyfriend that were used to launder part of ($182.8 million) the proceeds from the original romance scam.
That the Thai law-enforcement are still working this case (with results) after so many years it important for Thailand as is ensures they do not get stuck with a reputation as a nexus for romance-scam operators.
Further reading: The Record, The Bangkok Post, ABC
Cybersecurity Threat Landscape
Cracked[.]io and Nulled[.]to forums seized, 2 individuals arrested, 12 domains
Two well-known sites cracked[.]io and nulled[.]to that operated under a thin guise of sometimes offering ethical hacking discussions have been seized by law-enforcement in "Operation Talent" involving multiple agencies.
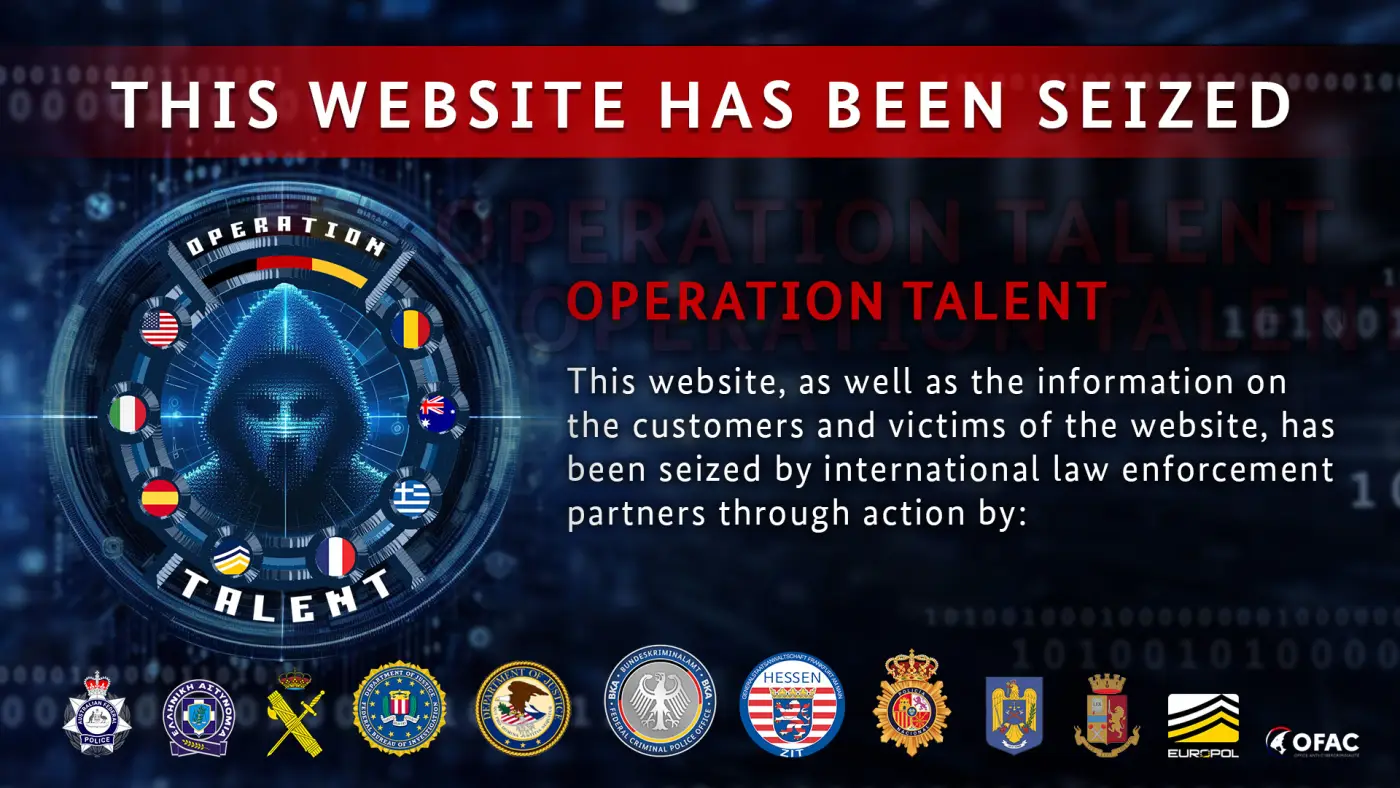
The two platforms, with a combined user base of ~10 million users acted as an easy entry point into learning cybercrime and connecting with other willing cybercrime participants. Both sites also operated as marketplaces for illegal goods, cybercrime-as-a-service, stolen data, malware and hacking-tools.
The United States Department of Justice stated that -
[Cracked] generated approximately $4 million in revenue, and impacted at least 17 million victims from the United States,
and
[Nulled] listed over 43 million posts advertising cybercrime tools and stolen information, and generated approximately $1 million in yearly revenue
Further reading: Krebs on Security, Hack Read, The Record
Backdoors found on Juniper routers use magic-packets for stealthy reverse-shell access
Cybersecurity lab "Black Lotus Labs" has posted an extraordinary article uncovering a VPN backdoor (they have named J-Magic) found to be installed on large scale enterprise Juniper routers - the type of thing we really care about.
It is not currently known how the initial access is achieved, however once loaded it remains in memory and watches specially formed TCP packets to arrive. When one of these magic packets arrive a full TCP connection is established and then a challenge-response handshake takes place that protects their access. The external threat-actor then gets a reverse shell to the Juniper appliance.
Black Lotus Labs states that the victims are worldwide with evidence of companies in the US, UK, Norway, the Netherlands, Russia, Armenia, Brazil, and Colombia all impacted, spanning industries such as fiber optics, solar panel manufacturing, heavy machinery manufacturing, commercial boats and ferries, energy, technology, and semiconductor firms.
Check out the excellent indicators of compromise that can be used by defenders published on Github.
Further reading: Lumen, The Register, Ars Technica, Security Affairs
Cybersecurity Vulnerabilities
SonicWall critical vulnerability (CVSS 9.8)
Pre-authentication deserialization of untrusted data vulnerability has been identified in the SMA1000 Appliance Management Console (AMC) and Central Management Console (CMC), which in specific conditions could potentially enable a remote unauthenticated attacker to execute arbitrary OS commands.
Not to give SonicWall much space here, however noticing that a deserialization vulnerability can exist in the software of a security-appliance in 2025 underscores how tricky these issues can be as objects get passed deep into software stacks without developers noticing their (untrusted) data paths.
Further reading: SonicWall, CVE-2025-23006, Security Week,
Netgear WiFi router critical vulnerabilities (CVSS 7.6)
NETGEAR XR1000 before 1.0.0.74, XR1000v2 before 1.1.0.22, and XR500 before 2.3.2.134 allow remote code execution by unauthenticated users.
Further reading: CVE-2025-25246, Cyber Security News, Bleeping Computer
Apple zero-day vulnerability actively exploited (CVSS 7.3)
A use after free issue vulnerability has been fixed in visionOS 2.3, iOS 18.3 and iPadOS 18.3, macOS Sequoia 15.3, watchOS 11.3, tvOS 18.3.
A malicious application may be able to elevate privileges. Apple is aware of a report that this issue may have been actively exploited against versions of iOS before iOS 17.2.
Further reading: Apple, CVE-2025-24085, The Hacker News, The Register
