CyberSecurity.PH #042
Multiple APT groups using Windows shortcut exploit; Chain of compromised GitHub Actions; MS365 accounts targeted via OAuth; Apache Tomcat remote code execution; Velociraptor triage collector for Windows; Threat hunting for suspect M365 OAuth Apps
Welcome to CyberSecurity.PH issue #042,
Cybersecurity Threat Landscape
Multiple APT groups using Windows shortcut exploit with no Microsoft fix available
Eleven well known state-sponsored nation-state threat actors from North Korea, Iran, Russia and China are exploiting a vulnerability with .lnk files, common in Microsoft Windows to hide malware infection payloads.
A detailed report from Trend Micro Zero Day Initiative (ZDI) outlines their efforts in collecting more than 1000 real-world live samples of such .lnk files targeting -
- Government, military and defense organizations
- Finance and cryptocurrency-related organizations
- Think tanks and non-governmental organizations (NGOs)
- Telecommunications organizations
- Energy organizations
The Trend Micro ZDI report states -
We discovered nearly a thousand Shell Link (.lnk) samples that exploit ZDI-CAN-25373; however, it is probable that the total number of exploitation attempts are much higher. Subsequently, we submitted a proof-of-concept exploit through Trend ZDI's bug bounty program to Microsoft, who declined to address this vulnerability with a security patch.
At least one target in the Philippines among the Trend Micro detected dataset.
The issue itself is rather "boring" since it simply uses whitespace characters to push arguments in the .lnk file out of sight in the Windows user-interface - this simplicity when combined with authentic looking icons makes these .lnk files difficult for average Windows users to notice they contain malicious payloads - this unfortunately makes the technique quite effective.
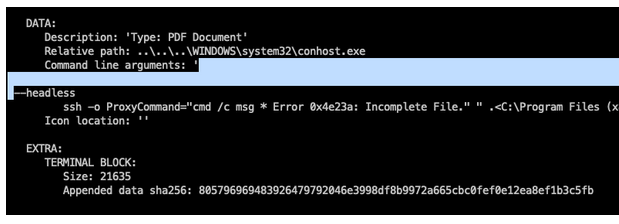
The report provides indicators-of-compromise and common threat detection rules to help defenders catch these threats.
Further reading: Trend Micro, The Record, Bleeping Computer, The Register, Dark Reading
Compromised GitHub Action leads to further GitHub Action compromises
Earlier this week Github Action tj-actions/changed-files was identified as having been compromised in a way where additional code was included into the action that causes run-time secrets to be dumped out for logging - thereby making those secrets observable to anyone checking those (public) logs.
The compromise of tj-actions/changed-files is notable because 23k other Github projects use this action to help manage their Github workflows - these projects are now impacted.
According to a report by cybersecurity company Wiz, it is now apparent that tj-actions/changed-files itself was compromised by another Github Action reviewdog/action-setup
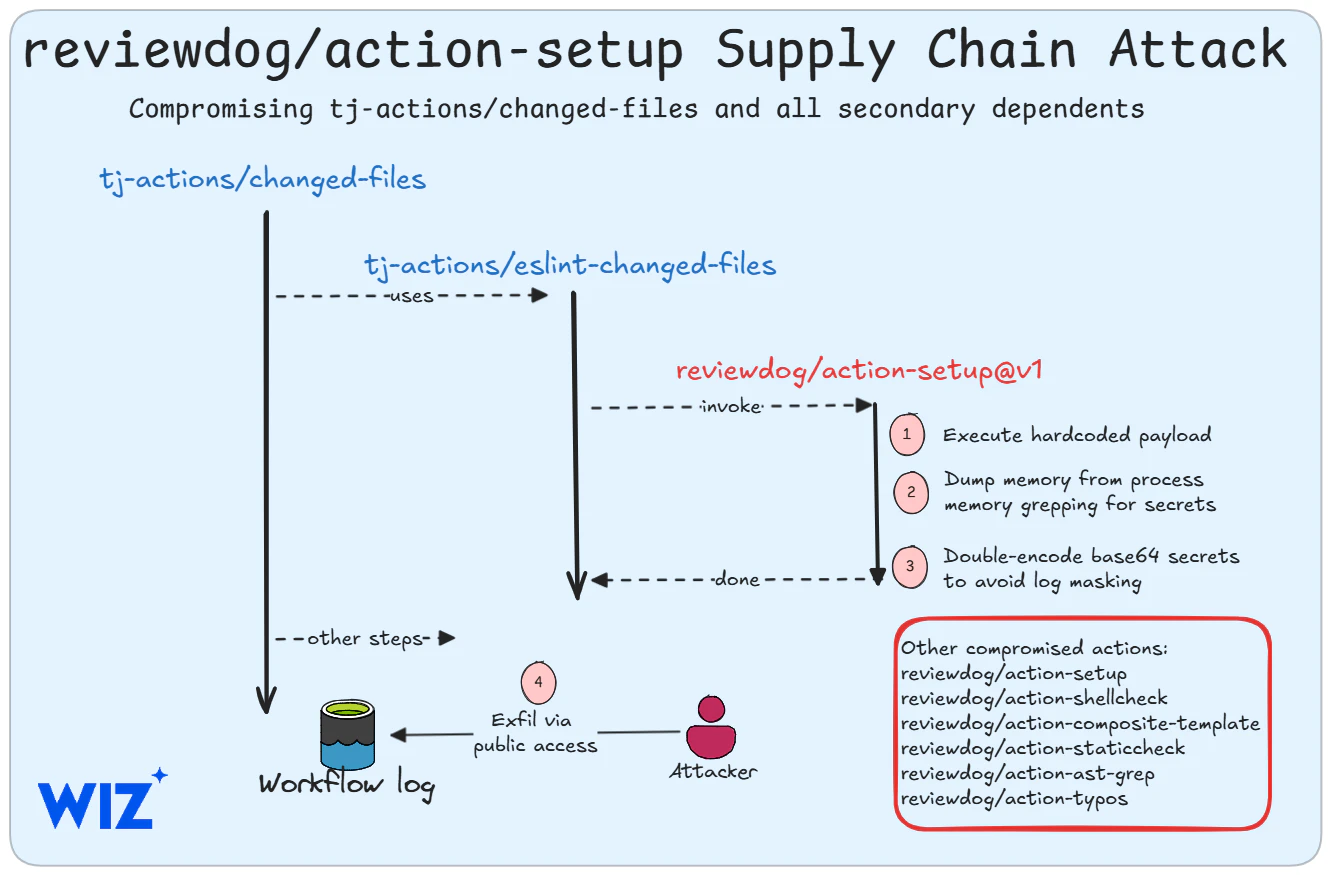
To the credit of ReviewDog they are providing up-to-date details on what has occurred and what they know in order to help other impacted projects respond and remediate.
A contributing factor in this event is that a malicious third party has been able to adjust the ReviewDog code and then tag the new code with a previous tag (this is the way git works) and because most folks to pin-by-tag, not pin-by-hash, their projects are pulling in those newly re-tagged but compromised Github Actions.
Plenty of additional reading on this matter - CISA.gov, Wiz.io, StepSecurity, Bleeping Computer
Authentic looking Adobe OAuth and DocuSign OAuth targeting Microsoft 365 accounts
Cybersecurity company Proofpoint have been sounding the alarm regarding their observations of threat-actors sending victims Microsoft OAuth requests for apps that masquerade as Adobe or Docusign that cause victims to authorize and visit those links.
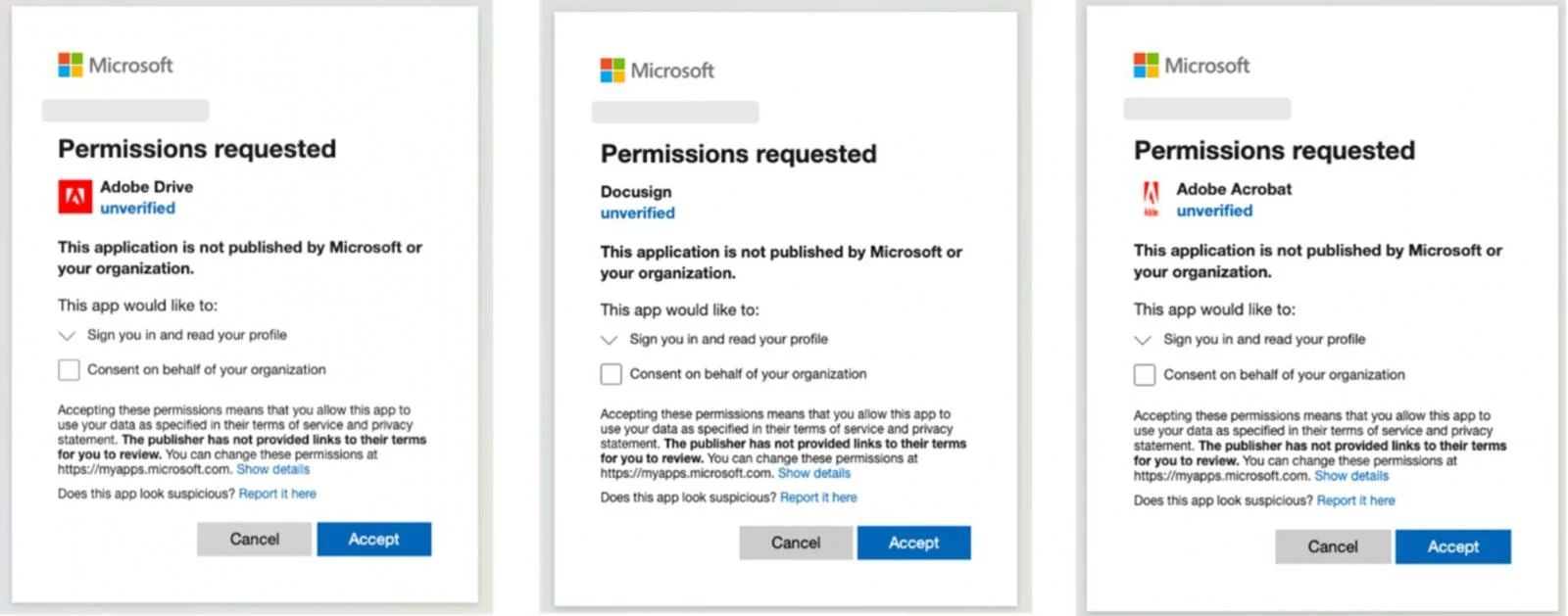
The difference with this campaign is that the OAuth requests ask for very basic and minimal permissions - hidden behind this layer of authentication is the payload that attempts to trick the victim with a "ClickFix" are-you-human interaction.
Placing the ClickFix behind an authentication layer like this makes it much harder for threat detection tools and threat detection systems to observe and catch the threat.
Further reading - Bleeping Computer, Cybersecuritynews
Cybersecurity Tools and Engineering
- Digital-Defense-Institute/triage.zip - provides an out-of-the-box Velociraptor triage collector for Windows, pre-configured for rapid and effective incident response - github.com/Digital-Defense-Institute/triage.zip
- HuskyHacks/cazadora - Threat hunting script for examining suspect M365 OAuth Apps - github.com/HuskyHacks/cazadora
- arsolutioner/ExtensionHound - security analysis tool that identifies DNS queries made by browser extensions, empowering security teams to detect and investigate suspicious activities - github.com/arsolutioner/ExtensionHound
Cybersecurity Vulnerabilities
Apache Tomcat remote code execution (CVSS 9.8)
CVE-2025-24813: exploit requires two steps, first, the threat-actors upload a serialized Java session file with a PUT request, then the threat-actor triggers a deserialization by referencing the malicious session ID in a GET request - leads to full remote code execution.
Further reading - Apache, Bleeping Computer, The Register, Dark Reading
PHP remote code execution vulnerability exploited in new attacks (CVSS 9.8)
CVE-2024-4577: remote code execution vulnerability affecting PHP installations on Windows when CGI mode is enabled. Allows threat-actors to execute arbitrary code on the server by exploiting character encoding conversion.
This vulnerability while patched by PHP last year is still very common among deployed web servers and is thus being actively exploited.
Further reading - The Record, Cisco Talos, Bleeping Computer
Microsoft March 2025 Patch Tuesday: Fixes 57 vulnerabilities 6 of them being zero-days
Microsoft has released their March 2025 security updates that fix 57 security vulnerabilities in its software with 6 of them being zero-day issues that are stated to be actively exploited in the wild - this makes the largest collection of zero-day issues in a single Microsoft patch-collection.
Among the 56 vulnerabilities, 6 are rated critical, 50 are rated Important, and one is rated Low. 23 of the vulnerabilities are remote code executions and 22 are privilege escalations.
Further reading - Microsoft, Krebs on Security, Hack Read, Bleeping Computer
