CyberSecurity.PH #010
Undocumented MultiLogin Google OAuth endpoint; Actively exploited vulnerabilities in Chrome and MS Excel parser; Online scams in Philippines highest in Asia; Awesome Nuclei Templates Collection
Philippines
Online scams in Philippines highest in Asia
The Global Anti-Scam Alliance (GASA) based in the Netherlands, together with Taiwan-based company Gogolook, recently produced a report titled Asia Scam Report 2023 (registration) that provides a deep-dive examination into scams and frauds in the Asia region. The report highlights (page 19) that the Philippines suffers the highest rates of online-shopping scams and investment-scams in the Asia region.
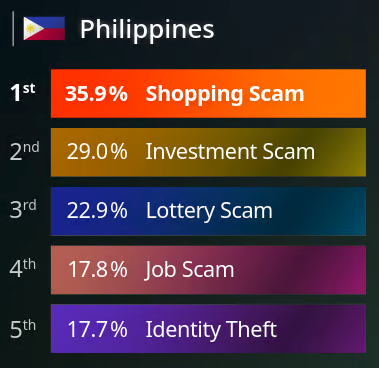
Helping Filipinos understand cyber security concepts even in small ways is fundamental to reducing the rate of PH scam victims . We now have a Learning Materials section on CyberSecurity.PH to help a wide range of people with different levels of technology literacy. Check it out!
Cybersecurity Threat Landscape
Undocumented MultiLogin Google OAuth endpoint enables old authentication cookies to be reactivated after password reset
Reported that info-stealer malware has been exploiting an undocumented Google OAuth endpoint that allows threat-actors to reactivate old authentication cookies even after Google victims have changed their account credentials; thus allowing threat actors re establish account access.
Cybersecurity company CloudSEK has as published a detailed analysis that describe how the malware(s) work and the associated Google OAuth endpoint that is abused to gain the reactivation effect - cloudsek.com/blog
Google advises that users MUST actively logout of sessions to invalidate associated authentication cookies; changing passwords is not enough.
Additional reporting - Bleeping Computer, Dark Reading, The Register
Microsoft disables app installation feature abused by hackers
Reported that Microsoft Threat Intelligence has been observing well known APT actors using the ms-appinstaller URI scheme to distribute malware. In response to this activity, Microsoft has disabled the protocol feature.
The screenshot samples provided in the Microsoft report provide convincing Windows user dialogue screens that easily trick most users because the visual indicators and verifiers to end users are limited - microsoft.com
Additional reporting - The Record, Bleeping Computer
CISA warns of actively exploited vulnerabilities in Chrome and a Perl parsing library for MS Excel
CISA has added two new vulnerabilities to its Known Exploited Vulnerabilities Catalog, based on evidence of active exploitation.
- CVE-2023-7024 Google Chromium WebRTC Heap Buffer Overflow Vulnerability
- CVE-2023-7101 Spreadsheet::ParseExcel Remote Code Execution Vulnerability
The “Spreadsheet::ParseExcel” vulnerability is the issue behind the recent Barracuda Email Security Gateway exploits that we reported on last week.
Cybersecurity Engineering
A weekly highlight on tools and other resources (often open-source) that we use, find useful or is just plain interesting; check out our engineering-section online at CyberSecurity.PH too!
- Prowler - Open Source security tool to perform AWS, GCP and Azure security best practices assessments, audits, incident response, continuous monitoring, hardening and forensics readiness - https://github.com/prowler-cloud/prowler
- Terrapin Scanner - a small utility program that can be used to determine the vulnerability of an SSH client or server against the Terrapin Attack - https://github.com/RUB-NDS/Terrapin-Scanner
- Nuclei Templates Collection - the largest collection of Nuclei templates we’ve seen yet, includes a handy de-duplication tool too - https://github.com/emadshanab/Nuclei-Templates-Collection
Cybersecurity Engineering Overload
This week we’ve introduced a new section called “Cybersecurity Engineering Overload” to deal with especially technical items.
Operation Triangulation: What You Get When Attack iPhones of Researchers
Awesome presentation at 37C3 that goes into detail on how the “Extraordinary iPhone hack exploited hidden hardware feature for zero-click remote backdoor” issue was detected, captured and reverse engineered. It’s a full hour, you’ll need to make yourself some time to watch - youtube.com/watch
Google OAuth is (sort of) broken
An excellent write up by Dylan Ayrey from Truffle Security describing an issue that can allow employees at companies to retain indefinite access to applications like Slack and Zoom, after they’re off-boarded and removed from their company’s Google organization. The vulnerability is easy for a non-technical audience to understand and exploit - trufflesecurity.com/blog
Got news or something you’d like us to mention, feel free to get in contact - [email protected]
