CyberSecurity.PH #019
Reported Philippine Statistics Authority (PSA) data leak; vulnerable Microsoft Exchange servers; US agency scolds Microsoft on substandard cloud security; Phishing-as-a-service MFA bypass; Supply chain attack on SSH inserts backdoor via XZ library
Philippines
PBBM urges Army forces to bolster cybersecurity capabilities
President Ferdinand R. Marcos Jr. (PBBM) has called on the Philippine Army to boost cybersecurity capabilities and adopt new cybersecurity technologies through increased collaboration with other major services of the Armed Forces of the Philippines (AFP), and through improved cooperation with Philippine defense allies.
Presidential Communications Office of the Philippines
Twitter report of Philippine Statistics Authority (PSA) data leak
Twitter identity Deep Web Konek claim the Philippine Statistics Authority (PSA) has been compromised with a 152GB leak of Philippine Citizen Identity Card data leaked.
Currently no official information from the PSA at this early stage; the story, if accurate, is still developing - until the PSA confirm it, it’s just a Tweet.
While “Deep Web Konek” is not an official or authoritative news source, their posts and claims have been accurate in the past.
https://twitter.com/deepwebkonek/status/1775428452654743607
UPDATE 2024-04-04: the original Tweet (above) has been removed by DWK and an apology posted
Deep Web Konek (DWK) acknowledges the dissemination of inaccurate information regarding the Philippine Citizen ID. We retract all related content and express sincere regret for any confusion caused. Committed to upholding accuracy and integrity.
— Deep Web Konek (@deepwebkonek)
12:00 PM • Apr 4, 2024
Cybersecurity Threat Landscape
German cyber agency warns 37% of Microsoft Exchange servers are vulnerable to critical bugs
According to a report by the German Federal Office for Information Security (BSI), ~37% of Microsoft Exchange servers are vulnerable to one or more critical bugs, and cyber-threat actors are already actively exploiting several of their vulnerabilities to deliver malware and carry out cyber espionage and ransomware attacks.
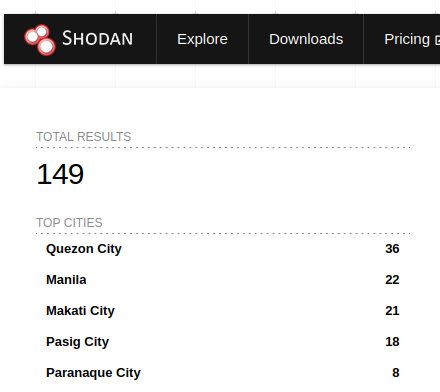
A straight forward query using public access Shodan.io indicates a similar percentage rate applies to Microsoft Exchange servers observable in the Philippines.
Microsoft told to clean up substandard cloud cybersecurity by US federal review board
A United States federal review board has called on Microsoft to clean up their substandard cloud cybersecurity practices and stop playing customer tricks by pushing cybersecurity burden to customers in the wake of a July 2023 cyberattack that let Chinese threat actors breach Microsoft 365 accounts to spy on key US government officials.
The report released on April 2, 2024 by the independent Department of Homeland Security (DHS) Cyber Safety Review Board offered an incendiary review of Microsoft's security culture, putting the blame squarely on the company and a "cascade of security failures" for the cyber espionage attack by China-based threat group Storm-0558, which "never should have happened."
Dark Reading, Bleeping Computer, The Record
Apple account “MFA Bombing” targeting users to cause account compromise
Brian Krebs from Krebs of Security reports “… elaborate phishing attacks that involve what appears to be a bug in Apple’s password reset feature. In this scenario, a target’s Apple devices are forced to display dozens of system-level prompts that prevent the devices from being used until the recipient responds “Allow” or “Don’t Allow” to each prompt. Assuming the user manages not to fat-finger the wrong button on the umpteenth password reset request, the scammers will then call the victim while spoofing Apple support in the caller ID, saying the user’s account is under attack and that Apple support needs to “verify” a one-time code…”
Phishing-as-a-service (PhaaS) platform “Tycoon 2FA” designed to bypass MFA targets Microsoft 365 and Gmail accounts
Cyber threat actors are using a phishing-as-a-service (PhaaS) platform “Tycoon 2FA” to target Microsoft 365 and Google accounts to bypass two-factor authentication (2FA) protection according to a report by Sekoia.
Tycoon 2FA was discovered by Sekoia analysts in October 2023, however it has been active since at least August 2023, when the Saad Tycoon group offered it through private Telegram channels.
Free VPN apps on Google Play silently turn Android phones into network proxies
A report published by HUMAN's Satori threat intelligence team lists 28 applications on Google Play that secretly turned Android devices into proxy servers that can be used by threat actors to compromise systems behind firewalls.
The following apps were uncovered and taken down as part of the HUMAN investigation
Lite VPN, Anims Keyboard, Blaze Stride, Byte Blade VPN, Android 12 Launcher, Android 13 Launcher, Android 14 Launcher, CaptainDroid Feeds, Free Old Classic Movies, Phone Comparison, Fast Fly VPN, Fast Fox VPN, Fast Line VPN, Funny Char Ging Animation, Limo Edges, Oko VPN, Phone App Launcher, Quick Flow VPN, Sample VPN, Secure Thunder, Shine Secure, Speed Surf, Swift Shield VPN, Turbo Track VPN, Turbo Tunnel VPN, Yellow Flash VPN, VPN Ultra, Run VPN
Discord Bot Python SDK modified to include a fake Colorama package with malware from a fake typo-squatted PyPi repo
Reported by the Checkmarx Research team; a recently discovered attack campaign targeting the software supply chain of a popular Discord bot SDK (Top.gg) has impacted multiple victims. Threat actors used multiple TTPs in this attack, including account takeover via stolen browser cookies, contributing malicious code with verified commits, setting up a custom Python mirror, and publishing malicious packages to the PyPi registry.
Checkmarx, The Record, Bleeping Computer
Cybersecurity Engineering
A weekly highlight on tools and other resources (often open-source) that we use, find useful or is just plain interesting; check out our engineering-section online at CyberSecurity.PH too!
Google Chrome implements “'Device Bound Session Credentials” using TPM to sign session-auth cookies
Google have a prototype implementation of a feature in Google Chrome that signs session authentication cookies using the device TPM thus making those cookies useless if stolen.
It’s early days for the feature yet but the technique is promising to address the threat of stolen session cookies that is rapidly becoming a common threat vector and increasingly hard to defend against.
Cybersecurity Vulnerabilities
Supply chain attack on SSH inserts malicious backdoor code via XZ library
This might be the biggest news of the year, that it appears here in the last section does not do it justice - it’s a really big deal because it impacts SSH that is often trusted to be placed in internet addressable network positions and act as system admin gateways into large networks.
While we generally have a very low cybersecurity opinion of Microsoft products, we are in deep debt to Microsoft developer Andres Freund who took an extended journey to discover the issue - without his dedication this backdoor may not have been found for a long time - kudos to Andres here.
The issue (CVE-2024-3094) is that malicious code was introduced into upstream tarballs of the xz package, starting with version 5.6.0, and through a series of obfuscations a modification in the functions of the liblzma code, this can then be used by any software linked against this library… such as SSH.
It’s wild and very real; fortunately the Linux distributions that had started shipping versions 5.6.0 and 5.6.1 of the xz package are quite limited so the blast radius is not nearly as large as it might otherwise have been.
An overflow of information on this issue; CISA, Dark Reading, Wikipedia, The Register, The Record, Bleeping Computer
Microsoft SharePoint RCE vulnerabilities actively exploited
Microsoft continue to demonstrate they are the largest supply-chain-threat vendor with a pair of MS Sharepoint vulnerabilities now actively exploited by threat actors to achieve RCE on vulnerable systems according to CISA.
- CVE-2023-29357 Microsoft SharePoint Server Privilege Escalation Vulnerability - cisa.gov
- CVE-2023-24955 Microsoft SharePoint Server Code Injection Vulnerability - cisa.gov
Got news or something you’d like us to mention, feel free to get in contact - [email protected]
