CyberSecurity.PH #015
PBBM approves National Cybersecurity Plan 2024; Espionage group observed using USB devices to hack targets in the Philippines; Microsoft is the supply chain threat, New critical Exchange bug exploited as zero-day; more awesome Cybersecurity Engineering tools
Philippines
PBBM approves National Cybersecurity Plan 2024-2029
Announced by DICT Secretary Ivan John Uy at a press briefing in Malacañang on Thursday, president Ferdinand R. Marcos Jr. (PBBM) has approved the National Cybersecurity Plan 2024-2029 to provide the Philippines with policy direction and operational guidelines in building its cybersecurity posture - PCO.gov.ph
The plan itself has not yet been made publicly available on the DICT website as of this writing. The older 2022 plan is still listed.
Espionage group observed using USB devices to hack targets in the Philippines
Cybersecurity firm, Mandiant reported back in November 2022 (~15 months ago) their identification of cyber espionage activity that heavily leverages USB devices as an initial infection vector; concentrates on targets in the Philippines; assessed as having a China based nexus; and is tracked as UNC4191.
This active threat scenario underscores the hazards in using USB thumb drives to transfer files between parties, especially when they occur via parties that “require” data to be supplied via USB as they become malware super spreaders.
Certain government departments in the Philippines are known for requiring form submissions to be supplied and exchanged via USB thumb drives and in doing so are placing their communities at much increased cybersecurity risks and hazard.
Additional reading - Mandiant
Cybersecurity Threat Landscape
Nation-States Are Weaponizing AI in Cyberattacks
Nation-state actors from Russia, North Korea, Iran, and China are already leveraging large language models (LLMs) to enhance ongoing cyber threat operations.
A report from OpenAI states they have disrupted efforts made by five state-affiliated actors that used its AI services to perform malicious cyber activities by terminating their assets and accounts.
Additional reading - OpenAI, The Hacker News, Dark Reading
Microsoft is the supply chain threat; New critical Exchange bug exploited as zero-day
Microsoft announced on Wednesday that this month's Patch Tuesday patched an actively exploited zero-day vulnerability in Microsoft Exchange Server.
The issue, CVE-2024-21410, carries a CVSS of 9.1 allows remote unauthenticated threat actors to escalate privileges on vulnerable Microsoft Exchange Servers in an NTLM relay attack.
Additional reading - The Hacker News, Bleeping Computer
Fake LastPass password manager observed in Apple App Store
LastPass are reporting of a look-a-like app that is attempting to impersonate the original.
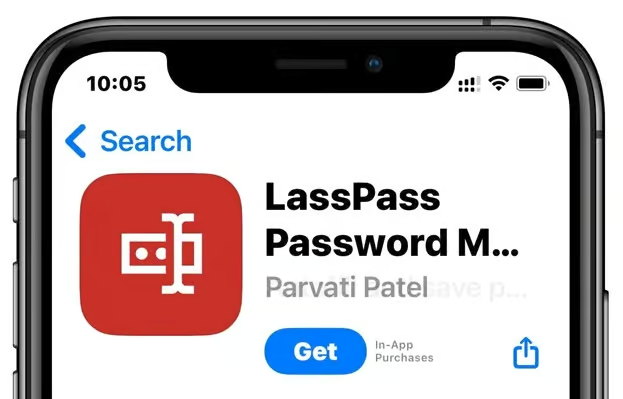
The fake-app attempts to copy LastPass branding and the posted screenshots reveal misspellings and other indicators the app is fraudulent.
Additional reading - LastPass, Bleeping Computer, The Register
CISA warns of Fortinet vulnerability being exploited in the wild
Cybersecurity and Infrastructure Security Agency (CISA) have added CVE-2024-21762 (Fortinet FortiOS Out-of-Bound Write Vulnerability) to their list of known exploited vulnerabilities - CISA.gov
Of note here is that CISA usually issue directives with a 21 day time-to-patch deadline for their audience. The directive attached to this issue was issued with a 7 day time-to-patch.
Fortinet appliances have more than one current high range vulnerability to patch at the moment, CVE-2024-23313 that carries a CVSS of 9.8 also requires urgent attention.
Additional reading - The Record, Bleeping Computer
Cybersecurity Engineering
A weekly highlight on tools and other resources (often open-source) that we use, find useful or is just plain interesting; check out our engineering-section online at CyberSecurity.PH too!
- eizedev/MSSecurityVulnerabilities - Getting straightforward information from Microsoft on vulnerabilities can be arduous, this PowerShell module makes it easier to retrieve Microsoft security vulnerability information https://github.com/eizedev/MSSecurityVulnerabilities
- Ostorlab/KEV - Awesome collection of Nuclei templates to detect most remotely known exploitable vulnerabilities. Sourced from CISA KEV, Google's Tsunami, Ostorlab's Asteroid and Bug Bounty programs https://github.com/Ostorlab/KEV
- Infisical - an open-source secret management platform for DevOps teams, Sync secrets across your team/infrastructure and prevent secret leaks https://github.com/Infisical/infisical
Cybersecurity Vulnerabilities
Critical Microsoft Outlook RCE bug, trivial to exploit using a !
Checkpoint have released an article that describes their discovery of an MS Outlook vulnerability CVE-2024-21413 (CVSS 9.8) that leads to a full remote-code-execution - Checkpoint
Patch now, don’t allow your users to update later.
Additional reading - Bleeping Computer, CISA.gov
Zoom patches privilege escalation vulnerabilities in Windows apps
The security team at Zoom have discovered a vulnerability (CVE-2024-24691) that impacts their Zoom Desktop, Zoom VDI Client, Zoom Rooms and Zoom Meeting software that carry a CVSS of 9.6.
The latest Zoom software patches 6x vulnerabilities, time to update.
Additional reading - Bleeping Computer
Got news or something you’d like us to mention, feel free to get in contact - [email protected]
