CyberSecurity.PH #013
Open source threat intel feeds; a 26 billion records data breach collection; Microsoft hacked yet again by Russian intelligence group; Authentication bypass in GoAnywhere; New government office for cyber threats in the Philippines
Philippines
PBBM forms Office for Cyber and Emerging Threats
Philippine president Ferdinand R. Marcos Jr. (PBBM) has reorganized the National Intelligence Coordinating Agency (NICA) to establish the Office of the Deputy Director General (ODDG) for Cyber and Emerging Threats under the NICA with Executive Order (EO) 54. The ODDG for Cyber and Emerging Threats, will be headed by a Deputy Director General with the rank of Assistant Secretary to be appointed by the President.
Additional reading - Philippine News Agency, PhilStar, Manila Bulletin
PLDT becomes first Philippine organization to join FIRST cyber incident response network
PLDT reports that it has become the first Philippine organization to join the international Forum of Incident Response and Security Teams (FIRST) that operates to reduce threats, build trust, and make relationships between nation states more predictable.
This is a positive development for the Philippines and paves the way for other Computer Incident Response Teams (CIRT) defending national infrastructure in the Philippines to also join FIRST.
Additional reading - Manila Bulletin
Cybersecurity Threat Landscape
12TB with 26 billion records “MOAB” data breach collection
This week, security researchers from Security Discovery and CyberNews have uncovered a database of leaked data that is 12 terabytes with 26 billion records - CyberNews
The scale of the dataset is staggering with 3800 individual folders that represent a data breach each. The dataset is stated to include records of various international government organizations including the Philippines.
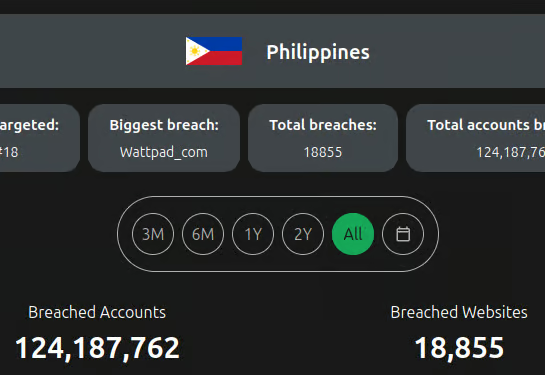
A review of the CyberNews dataleak checker indicates that over 120M records impacting the Philippines are present in the data tracked by CyberNews.
Additional reading - Forbes
Microsoft Executive Emails Hacked By Russian Intelligence Group
Microsoft has announced that known Russian cyber threat group Nobelium (also known as APT29 or Cozy Bear) have been accessing Microsoft executive staff emails since November 2023.
The technique used to gain access involved a basic password-spray against a legacy/test system that had been kept running by Microsoft and lacked any 2FA protections. This access then provided threat actors a pivot point to move into Microsoft internal corporate environments.
The incident has drawn sharp criticism from various Microsoft critics that call the lapse inexcusable for a company that has security responsibilities involving the national defense departments of several countries.
Additional reading - CyberScoop, The Register, Bleeping Computer
UK, US and Australia sanction Russian citizen over data hack
Australian authorities have named Aleksandr Gennadievich Ermakov a Russian national and a member of the REvil cyber gang as being a key figure in a data hack event that impacted almost 10M Australians.
The trilateral sanction response among Australia, United Kingdom and the United States is the first such coordinated response action and underscores the collective resolve to hold cyber criminals to account.
This coordinated action also highlights the importance of strong relationships with partner countries that have capacity to bring powerful action against cyber threat actors that personally impact threat-actors and their future.
Additional reading - The Record, Dark Reading, The Register
Cybersecurity Engineering
A weekly highlight on tools and other resources (often open-source) that we use, find useful or is just plain interesting; check out our engineering-section online at CyberSecurity.PH too!
- Open-Source-Threat-Intel-Feeds - an awesome collection of freely usable Threat Intel feeds that can be used without additional requirements. Contains multiple IPs, URLs, CVEs and Hashes - https://github.com/Bert-JanP/Open-Source-Threat-Intel-Feeds
- CloudCatalog - defending AWS infrastructure requires identifying and documenting the resources in use, CloudCatalog provides a decent tool to do just that - https://github.com/boyney123/cloudcatalog
- iShutdown - provides a straightforward set of Python scripts that can help determine if an Apple device has been impacted by Pegasus from Israeli cyber-arms company NSO Group - https://github.com/KasperskyLab/iShutdown
Cybersecurity Vulnerabilities
Authentication Bypass in GoAnywhere MFT (CVE-2024-0204)
Reported that exploit code is now available for a critical authentication bypass vulnerability in Fortra's GoAnywhere MFT (Managed File Transfer) software that allows attackers to create new admin users on unpatched instances via the administration portal - Bleeping Computer
The issue CVE-2024-0204, carries a CVSS of 9.8 and is devastating for a platform that is positioned to manage enterprise wide cyber security.
Additional reading - Fortra, The Hacker News
Apple Webkit (Safari) zero-day vulnerability activity exploited
Apple has patched CVE-2024-23222 an actively exploited zero-day bug in its WebKit browser engine for Safari.
The issue has already been added by CISA to their catalog of known activity exploited vulnerabilities which implies exploits are in the wild and being used by threat actors.
Additional reading - Bleeping Computer, Dark Reading
Ivanti vulnerabilities widely exploited, CISA issues emergency directive
We first reported on the Ivanti vulnerabilities two weeks ago.
This week, US agency CISA has now issued an emergency directive to their audience indicating that Ivanti vulnerabilities are rapidly being exploited and must be patched immediately.
Our position would be that if you still have one of these appliances without being patched then you should treat it as already compromised.
Additional reporting - Bleeping Computer, The Record
Got news or something you’d like us to mention, feel free to get in contact - [email protected]
